16
Arnaut Aguilar
Strong chapter here. Just need to work on some of the details. Need to link the sources in reference list and then link to them in the internal citations. Need to be sure to create some links to keywords.
Introduction
How much do you care about your privacy online? We as a society value our privacy a lot; from buying curtains to tinted car windows, we do everything in our hands to keep our life on wraps to strangers. Since the start of the pandemic, we have seen our way of life shifting over more and more to the digital world. From school to work, we all have experienced an increase in the use of technology throughout the day. With this frequent use of technology connected to the internet, we also produce more data and leave more data around. This data could be public data such as the things you post on different social media, or it could be private such as your credit card number. This massive surge of new data and information online comes with a big surge of private information that mischievous people want to get a hold of. This could not only affect us personally but businesses could also be affected. Since the start of Covid-19 and quarantine, there have been multiple attacks worldwide on businesses and people. Not only have there been multiple attacks, but one of the largest scams pulled on Twitter also occurred during the pandemic. But there is a way to resolve it and the biggest demographic that is experiencing this surge in technology is college and university students. We will learn new ways of keeping information safe online.
Connection to STS Theory
The STS Theory that best relates to this topic is modernization theory. This theory explains the process of innovation and growth within society. Modernization is broken down into different eras, such as pre-modern, traditional, and modern. Not only does society go through these types of modernization, but things in our society do as well; in this case, it’s advancements in cyber technology. Previous to recent years, cyber technology hasn’t been available to our convenience, but that also means it also hasn’t posed a threat to our privacy nearly as much as it does in today’s society.
A Timeline of Cyber Attack Events
Throughout the pandemic, there have been multiple cyber attacks throughout the world, from Asia, Europe, and North America. We have experienced a great surge in cyberattacks this year alone compared to previous years. The cyberattacks being documented are between January and May. Some of the cyber attacks include: Chinese hackers accused of distributing the Vicious Panda malware to Mongolia through emails purporting to come from the Mongolian Ministry of affairs, phishing attacks on medical groups in China that were traced back to India, attack on a Chezch hospital and stealing the information from patients, and free Netflix offer directs users to a malware-ridden website. “The 43 cyber-attacks presented in the timeline can be further categorized as follows:
- 37 (86%) involved phishing and/or smishing
- 2 (5%) involved hacking
- 2 (5%) involved denial of service
- 28 (65%) involved malware
Out of these cybercrimes, they were then broken down into further categories:
- “15 (34%) involved financial fraud
- 6 (13%) involved pharming
- 6 (15%) involved extortion” (Lallie, Harjinder Singh 2020).
“Out of these 43 attacks, 25% of them have occurred in China, 14% in the United States, 14% in the UK, 17% global and 30% other.” (Lallie, Harjinder Singh 2020). It is very alarming to see how much has cyber attacks have increased. At some point, we will be able to know someone has been affected by a cyber attack. Based on the data, most cyberattacks deal with financial fraud and people have become fairly good at social engineering their way into a situation where they can get that sort of information.

The other section is for cyber attacks that could not be pinpointed to a certain location since they were done anonymously. The increase in cyber attacks is alarming, and it can be hazardous, like the Chezch hospital where they took patients’ information. With just a little bit of access to a systems database, you can ruin the lives of multiple people with just a few clicks and types.
Voices of Clemson Undergraduate Students
“I really appreciate all the safety measures Clemson puts in for us to keep the school and our privacy safe.
The Bitcoin Scam of the Year
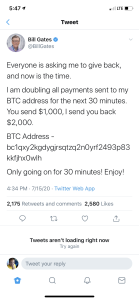
The event took place in July and it was a bitcoin scam. The hackers were able to gain access to the Twitter accounts of some of the most influential people at the moment. They then proceed to post on their accounts this bitcoin address so that they can gain money from their followers. “The Times verified that the four people were connected to the hack by matching their social media and cryptocurrency accounts to accounts that were involved with the events on Wednesday” (Popper, Nathaniel, and Kate Conger 2020). The three central peoples’ aliases are Kirk, lol, and ever so anxious. These were the main people who took control of Twitter accounts. Lol and ever so anxious only wanted to hack into Twitter accounts that had original names such as numbers or single letter usernames that were very sought after because they are original. “For online gamers, Twitter users and hackers, so-called O.G. user names — usually a short word or even a number — are hotly desired. These eye-catching handles are often snapped up by early adopters of a new online platform, the “original gangsters” of a fresh app” (Popper, Nathaniel, and Kate Conger 2020). On Wednesday morning, when the attacks were just about to start, ever so anxious had gone to sleep and was not a part of the take over of large accounts. That was when “Kirk quickly escalated his efforts, posting a message from accounts belonging to celebrities like Kanye West and tech titans like Jeff Bezos: Send Bitcoin to a specific account and your money would be sent back, doubled “(Popper, Nathaniel, and Kate Conger 2020). As soon as Kirk started going for high profile people lol and ever so anxious decided to cut ties with him. Later that night, Twitter was able to catch up with Kirk, and they were able to stop the posting of messages. They limited the number of users on Twitter as they tried fixing it over the next couple of days. Kirk had made a profit of 20 BTC, which is around 180,000 dollars in the short span the messages were up and then disappeared off of Discord where he would communicate with lol and ever so anxious. He later was discovered to be a 17-year-old male from Tampa, Florida. Just imagine, he was able to gain access to all of those accounts and get so much money in so little time. If he had performed the hack more discreetly, he could have gotten away with more money. This shows how important it is to keep passwords and sensitive information safe and more during this time since we do everything online.
Ways to maintain private information private for college students
Since everything has moved online, hackers want to capitalize on this surge of people moving on to unprotected online environments. Most people will not experience a big hack in which someone takes down their internet, but the most common type of hack is phishing. Phishing “is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message”(What Is Phishing 2020). Since most college students receive a multitude of emails and texts every day, they should be able to tell the difference. If not, here are a couple of tips for identifying phishing scams. “As the Phishing emails usually want you to click on something, for instance, to update your payment details, or access the latest information on COVID-19”(digitalLEARNING Network 2020). If you believe you may have been a part of a phishing scam, you should try to change your passwords to most important accounts that have information. Due to the pandemic, some phishing scams entice users to click on them with names such as “Eeskiri-COVID-19.chm” (digitalLEARNING Network 2020), this is actually a keylogger that documents every keystroke you type and it can be used to figure out your passwords to different accounts. Phishing emails also tend to look less official than an actual email from a company, so you can compare the suspected phishing email to an email that you have already received from the same company. There are also some other cybersecurity tips that you should always do, which are: “Enable multi-factor authentication wherever possible, adding another layer of security to any apps you use. Additionally, a password manager can help avoid risky behaviour such as saving or sharing credentials” (digitalLEARNING Network 2020). We use two-factor authentification here at Clemson: the DUO app that we have downloaded on our phones. Whenever we get on iRoar, we have to use our DUO account to receive a security pin to authorize us access. We also have to use DUO for Canvas/iRoar whenever we are on an unsecured internet such as home or coffee shops. “Try to use VPN solution with an encrypted network connection. It is

safe for the worker to access IT resources within the organisation and elsewhere on the internet” (digitalLEARNING Network 2020). Clemson CCIT also provides us with a free VPN we can use whenever we are not connected to eduroam to protect ourselves and the university. I would highly recommend you using this even when you are at home. Overall, college students are at risk of falling into the hands of hackers looking to make some quick cash but using the tips given.
Conclusion
The point of all this is to get people aware of their information online and to keep it safe. Not just because of the increase in cyberattacks due to the pandemic, but to overall have a better grasp on their private information. We should all be somewhat informed of different hacks such as social engineering and phishing, which are some of the most common out there and easiest to pull off. Now that you have seen what can be done with your information online, will you rethink everything you do?
References
Lallie, Harjinder Singh, et al. “Cyber Security in the Age of COVID-19: A Timeline and Analysis of Cyber-Crime and …..Cyber-Attacks during the Pandemic.” ArXiv.org, 21 June 2020, arxiv.org/abs/2006.11929.
Popper, Nathaniel, and Kate Conger. “Hackers Tell the Story of the Twitter Attack From the Inside.” The New York …..Times, The New York Times, 17 July 2020, www.nytimes.com/2020/07/17/technology/twitter-hackers- interview.html.
“What Is Phishing: Attack Techniques & Scam Examples: Imperva.” Learning Center, Imperva, 17 June 2020, …..www.imperva.com/learn/application-security/phishing-attack-scam/.
digitalLEARNING Network. (April 4, 2020). Corona Virus (Covid-19) Pandemic and Work from Home: Challenges of …..Cybercrimes and Cybersecurity. Digital Learning.https://advance.lexis.com/api/document?collection=news&id=urn:contentItem:5YKC-89X1-JB5M-W4MM-00000-00&context=1516831.
Images
Image 1: “Secure Cloud Computing” by FutUndBeidl is licensed under CC BY 2.0
Image 2: “Screenshot of Twitter Hack July 15 2020” by Duncan Rawlinson – Duncan.co is licensed under CC BY-NC 2.0
Image 3: “The great growling engine of change – technology. Alvin Toffler” by katerha is licensed under CC BY 2.0

